Meta title:
Best Practices & Tools for DPDP-Ready Data Handling (2025 Guide)
Meta description (155 chars): Get DPDP-ready fast. Practical best
practices plus DPCM, DPGR, DPAP, DPIA, DPTPA & CCM to operationalise
compliance.
Introduction: What “DPDP-ready” really means
India’s Digital Personal Data Protection
(DPDP) Act raises the bar on how organisations collect, use, store, share, and
delete personal data. Being “DPDP-ready” isn’t about adding a cookie banner or
rewriting a privacy policy—it’s about operationalising lawful
processing, purpose limitation, data minimisation, retention, rights
enablement, security safeguards, and audit-ready evidence across the full data
lifecycle.
This guide distils best practices
you can implement today and shows how our toolset—DPCM, DPGR, DPAP, DPIA,
DPTPA, and CCM—helps you automate the hard parts, prove compliance, and
scale with confidence.
DPDP-ready checklist
- Clear lawful basis per purpose (consent / deemed consent)
- Layered, multilingual notices with easy withdrawal
- Single source of truth for consent + exportable audit logs
- Data minimisation by design; defendable retention + deletion
- Rights handling (access, correction, erasure, portability) with
SLA governance
- Risk-tied security and periodic DPIAs
- Third-party oversight and offboarding discipline
- Web/app-edge compliance (cookies, tracking, preferences)
- Evidence pack you can hand a regulator—any day
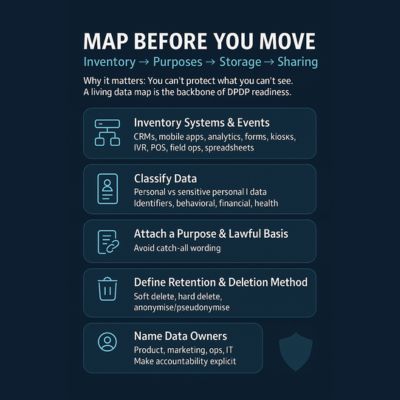
Map Before You Move: Inventory → Purposes → Storage → Sharing
Why it matters: You can’t protect what you can’t see. A living data map is the
backbone of DPDP readiness.
How to do it
- Inventory systems & events:
CRMs, mobile apps, analytics, forms, kiosks, IVR, POS, field ops,
spreadsheets.
- Classify data: personal vs
sensitive personal data; identifiers; behavioural; financial; health;
precise location.
- Attach a purpose & lawful basis
to each data element: avoid catch-all wording.
- Define retention & deletion method: soft delete, hard delete, anonymise/pseudonymise.
- Name data owners: product,
marketing, ops, IT; make accountability explicit.
Starter table
|
System
|
Data
|
Purpose
|
Lawful Basis
|
Retention
|
Owner
|
Risks
|
|
Mobile App
|
Phone, Email
|
Account creation
|
Consent
|
24 months after inactivity
|
Product
|
Stale accounts, weak auth
|
|
CRM
|
Full name, Phone
|
Sales follow-ups
|
Deemed consent (requested service)
|
12 months post-deal
|
Sales
|
Over-contacting, duplicate records
|
|
Analytics
|
Device ID
|
Usage analytics
|
Consent
|
13 months
|
Growth
|
Over-collection, cross-site tracking
|
Pro tip:
Keep this as a version-controlled sheet; add a cadence to review quarterly.

Consent & Deemed Consent—Get It Right and Prove It
Best practices
- Layered, plain-language notices
with just-in-time prompts (collect only what’s needed at that moment).
- Multilingual & accessible UI
(WCAG-friendly banners, keyboard navigation, screen reader text).
- Withdrawal = as easy as give (same
channel, minimal steps).
- Offline parity for
in-store/paper/field capture.
- Proof on file: timestamped consent
state, notice version, channel, actor ID.
Tool spotlight: DPCM — Data Principal
Consent Management
DPCM centralises legacy, paper, and live
consents in one system of record.
- Digitises and reconciles historical and paper consents
- Multilingual notices across web, app, IVR, kiosks, and field
ops
- Real-time APIs to propagate consent state instantly across
downstream systems
- Versioned policies + tamper-evident, timestamped audit logs
- Exportable consent evidence packs for audits
Outcome: One
truth for consent across channels, zero ambiguity, audit-ready proof.
See DPCM → Click Here

Data Minimisation & Retention You Can Defend
Minimise at collection
- Progressive profiling (collect more only when needed).
- Default-off fields; justify every field with a purpose tag.
- Separate “nice to have” from “must have”—and measure the
business impact of removing non-essential fields.
Retention that stands up to scrutiny
- Map legal/contractual drivers → set policy → enforce via
automation.
- Use deletion queues and review windows for high-risk data.
- Log every deletion/anonymisation event.
Retention table example
|
Data Type
|
Purpose
|
Lawful Basis
|
Retention
|
Trigger
|
Deletion Method
|
|
Lead email
|
Marketing offers
|
Consent
|
Until withdrawal or 12 months of inactivity
|
Inactivity tracker
|
Hard delete
|
|
KYC ID
|
Compliance
|
Legal obligation
|
8 years
|
Account closure + legal expiry
|
Secure archive then hard delete
|
|
Usage events
|
Analytics
|
Consent
|
13 months
|
Rolling window
|
Aggregation → anonymise
|

Rights Management (DPGR): Intake to Evidence, End-to-End
DPDP empowers Data Principals to access,
correct, erase, port, and raise grievances. The challenge is operational:
identity proofing with minimal data, SLA timers, orchestrating actions across
systems, and keeping evidence tidy.
Best practices
- Multi-channel intake (self-serve
portal, email, WhatsApp bot, call centre) with clear guidance.
- Identity proofing calibrated to
risk—collect the least additional information required.
- Clock management: when SLAs
start/stop, escalations, and exceptions.
- System orchestration: fetch data,
redact, correct, erase, port—then compile an evidence bundle.
Tool spotlight: DPGR — Data Principal
Grievance Redressal
- Guided intake flows + identity verification
- SLA governance, dashboards, and auto-escalations
- Connectors/APIs to read, redact, erase, or port data across
systems
- Full activity trail and downloadable closure reports
Outcome:
Faster, consistent rights handling with proof you can show a regulator.
See DPGR → Click Here

Build Culture: Awareness by Design (DPAP)
Technology fails when culture lags. Teams
need to know the “why,” “what,” and “how” of DPDP.
Tool spotlight: DPAP — Data Protection
Awareness Program
- Role-based micro-learning for product, marketing, sales,
support, field ops
- Policy attestations and refresher nudges embedded in daily
tools
- Training KPIs (coverage, quiz scores, overdue modules)
Outcome:
Lower breach risk, fewer mistakes, and better decisions at the edge.
See DPAP → Click Here
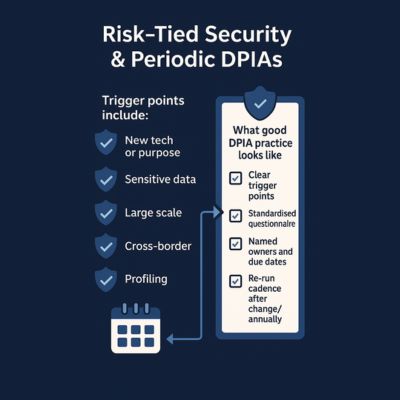
Risk-Tied Security & Periodic DPIAs
DPDP expects safeguards proportionate to
risk and context. Formal DPIAs are your engine to identify risks, decide
mitigations, and track outcomes.
What good DPIA practice looks like
- Clear trigger points (new tech, new purpose, sensitive data,
large scale, cross-border, profiling)
- Standardised questionnaire; objective scoring
- Named owners and due dates for mitigations
- Re-run cadence after material change or annually for high-risk
flows
Tool spotlight: DPIA — Data Protection
Impact Assessment
- Guided assessments with contextual hints and risk libraries
- Consistent scoring; mitigation plans linked to owners and
deadlines
- Portfolio dashboard to track risk heatmaps and residual risk
- Exportable DPIA reports for internal and external review
Outcome:
Continuous, auditable risk management—not one-off paperwork.
See DPIA → Click Here

Third-Party & Processor Governance (DPTPA)
Your compliance is only as strong as the
weakest vendor with your data.
Best practices
- Due-diligence questionnaires tailored by risk tier
- Evidence collection (policies, certifications, SOC/ISO reports)
- Risk scoring with remediation tracking and offboarding plans
- Notifications to third parties when Data Principal rights apply
to shared data
Tool spotlight: DPTPA — Data Protection
Third-Party Assessment
- Tiered DDQs, automated reminders, and document vault
- Risk scoring with heatmaps and remediation SLAs
- Connected to rights workflows where shared data is impacted
Outcome:
Visibility, leverage, and documented decisions across your vendor ecosystem.
See DPTPA → Click Here

Web/App-Edge Compliance: Cookies & Tracking (CCM)
Consent at the edge is visible to users and
regulators, so it must be done right.
Best practices
- Dynamic, multilingual banners with clear categories
- Prior blocking of non-essential
scripts until consent
- Granular preferences + easy change at any time
- Real-time consent logs tied to a user/device identifier
Tool spotlight: CCM — Cookie Consent
Management
- Fully compliant with DPDP, GDPR/ePrivacy, and CCPA/CPRA
- Auto-categorisation and automated prior blocking
- Preference centre + real-time consent logs; exportable evidence
Outcome:
Transparent UX and compliant tracking without analytics chaos.
See CCM → Click Here
Your DPDP-Ready Toolstack—At a Glance
|
Capability
|
Our Tool
|
Core Features
|
Lifecycle Fit
|
Evidence Produced
|
|
Consent management
|
DPCM
|
Legacy/paper/live consent; APIs; logs
|
Collection & changes
|
Consent logs, notice versions
|
|
Rights & grievances
|
DPGR
|
Intake→SLA→orchestration
|
Rights fulfilment
|
Request trail, ID proof, closure report
|
|
Awareness & training
|
DPAP
|
Role modules, attestations, KPIs
|
Culture & rollout
|
Training records
|
|
Impact assessments
|
DPIA
|
Guided DPIAs, scoring, mitigations
|
Design & risk mgmt
|
DPIA report, risk register
|
|
Third-party oversight
|
DPTPA
|
DDQs, evidence, risk SLAs
|
Vendor lifecycle
|
Risk scores, remediation logs
|
|
Cookie consent
|
CCM
|
Dynamic banners, blocking, logs
|
Web/app edge
|
Consent log exports
|

A Practical 90-Day DPDP Readiness Plan (with our tools)
Days 0–30 — Discover & Stabilise
- Build the data map (systems, data, purposes, retention, owners)
- Audit existing consent flows; fix obvious banner gaps
- Deploy CCM on web/app for prior blocking and logs
- Kick-off DPAP baseline training for key teams
Days 31–60 — Implement & Orchestrate
- Roll out DPCM to unify legacy + live consents; wire
critical systems via API
- Pilot DPGR for access/correction/erasure with SLA timers
- Run your first DPIA on the highest-risk processing
activity
- Start DPTPA with your top 10 vendors
Days 61–90 — Automate & Prove
- Standardise evidence packs (consent logs, rights bundles, DPIA
reports)
- Expand DPGR intake channels (WhatsApp/chat/call centre)
- Set a quarterly DPIA cadence for high-risk processes
- Vendor remediation SLAs tracked in DPTPA
CTA: Book a
30-minute DPDP Readiness Review and get our free templates pack →
/contact
KPIs that show you’re DPDP-ready
- Consent posture: ≥95% consent-log
coverage; ≤2 steps to withdraw via DPCM/CCM
- Rights performance: ≥90% on-time
closures; median time to fulfil ≤7 days via DPGR
- Risk cadence: Quarterly DPIAs for
high-risk processes via DPIA
- Vendor risk trend: Downward
trajectory in high-risk vendors; remediation SLA adherence via DPTPA
- Culture metrics: ≥95% training
completion; refresher rates ≥90% via DPAP
Common Pitfalls—and How to Avoid Them
- Banner ≠ compliance: Use DPCM
+ CCM for end-to-end consent and proof.
- Offline blind spots: Bring
paper/field consents into DPCM; reconcile routinely.
- Over-collecting identity for rights: Calibrate proofing in DPGR to the minimum needed.
- No deletion trail: Enforce
retention and log deletions.
- Weak vendor offboarding: Bake
offboarding checklists and data return/delete steps into DPTPA.
FAQs
1) What makes a data-handling process
“DPDP-ready”?
A lifecycle approach: lawful basis per purpose, data minimisation, retention +
deletion, rights enablement, risk-based safeguards, and evidence. Our
stack (DPCM, DPGR, DPAP, DPIA, DPTPA, CCM) operationalises each step.
2) Do I need consent for every purpose?
Not always. Map each purpose to the correct lawful basis (consent or deemed
consent) and document it. DPCM stores the state and proof.
3) How do I prove consent if audited?
Keep timestamped consent logs, tie them to notice versions and user
identifiers, and export evidence. DPCM/CCM handle this out-of-the-box.
4) How fast must I respond to rights
requests?
Follow your published SLAs and statutory timelines. DPGR sets timers,
automates escalations, and compiles closure evidence.
5) How often should we run DPIAs?
On triggers (new tech, sensitive data, profiling, scale) and on a periodic
cadence for high-risk processes. DPIA standardises and tracks this.
6) How do I manage third-party risk?
Use tiered questionnaires, collect evidence, score risk, and enforce
remediation/offboarding. DPTPA centralises it.
7) What about cookies across
geographies?
Implement dynamic, jurisdiction-aware banners with prior blocking and logs. CCM
supports DPDP, GDPR/ePrivacy, and CCPA/CPRA.
Conclusion & Next Steps
DPDP readiness is a discipline, not
a document. Start with the data map, lock down consent and cookies,
operationalise rights, harden your risk posture with DPIAs, govern vendors, and
keep your teams trained. With DPCM, DPGR, DPAP, DPIA, DPTPA, and CCM,
you can automate evidence, scale compliance, and focus on growth.
Read out more such article on DPDP
Consultants














